EU Horizon Infraestructure Defense
BLUE SHIELD-EU: AI-Powered Static Defense System for European Nuclear Facilities
Adapted for Horizon Europe and French Legal & Security Frameworks
Mission Objective
To protect Europe’s nuclear power plants from hybrid threats through a modular, AI-driven, and legally compliant static defense system. The architecture combines military-grade defense technologies with civil protection protocols and intelligent automation.
1. Intelligence-Enabled Infrastructure
- IIoT sensors for sabotage, radiation, and critical valve status
- IoT mesh for detecting anomalies (vibration, seismic, RF)
- Edge AI (Jetson/Movidius) for decentralized decisions
2. Physical Perimeter Security
- Triple-fencing with anti-climb/tunnel detection and smart mesh
- Seismic & buried sensors for footsteps and vehicle approach
- LIDAR/RADAR-assisted mapping & AI-CCTV with facial detection
- Automated sentry turrets (legal lethal & non-lethal options)
3. HUMINT + Behavioral AI
- Monitoring of employee stress, behavior, and radicalization
- Internal observer networks and behavioral AI analysis
4. SIGINT + OSINT + IMINT + MASINT
- SIGINT: SDR-based interception (GSM, SatCom, drone signals)
- OSINT: AI social media monitoring, sentiment tracking, darknet intel
- IMINT: Satellite/drone/thermal imagery with object recognition
- MASINT: Detection of chemical, thermal, acoustic, or radiation anomalies
5. Aerial & Artillery Threat Defense
A. Detection
- Counter-battery radar (GM200/GM400)
- 3D AESA radar and passive IR + acoustic array
- Swarm recognition using transformer-based neural networks
B. Neutralization
- Soft Kill: RF jammers, GPS spoofers, microwave pulses
- Hard Kill: HEL lasers, CIWS, SAM batteries (IRIS-T, Aster 15/30)
6. Cybersecurity & Electronic Warfare (EW)
- Zero-trust architecture for SCADA/ICS (Modbus, OPC-UA, IEC 61850)
- AI-based anomaly detection on industrial network traffic
- RF triangulation of hostile drone command centers
- Drone denial using HPM and passive jamming arrays
7. Command, Control & Simulation (C2-SIM)
- Digital twin of each facility for training, simulation & optimization
- Federated reinforcement learning models for each site
- EMP-shielded C2 rooms, redundant servers, autonomous fallback AI
8. Emergency & Response Integration
- Integration with GIGN and Plan ORSEC protocols
- AI-assisted evacuation and autonomous firefighting drones
- AR/VR crisis training and AI red-teaming simulations
9. Legal, Ethical & Environmental Compliance
- Full GDPR, CNIL, ASN, ANSSI alignment
- Encrypted black-box logs and third-party audit oversight
- REACH conformity for chemical systems
10. Deployment Roadmap (France)
| Site | Phase | Deployment | Timeline |
|---|---|---|---|
| Gravelines | Pilot | Full Blue Shield-EU Suite | Q4 2025 – Q2 2026 |
| Cattenom | Phase 2 | Aerial + EW Layers | Q2 2026 – Q4 2026 |
| Tricastin | Phase 3 | C2-AI Core + Intelligence Fusion | Q1 2027 |
| Flamanville | Phase 4 | Nationwide grid integration | Q2 2027+ |
Optional Add-ons (High-Risk Sites)
- Anti-tank bollards, drone-deployed smart mines
- Underwater acoustic sensors and sabotage detectors
- Airlock zones with biometric identity verification
Conclusion
BLUE SHIELD-EU delivers a resilient, modular, and intelligence-enriched defense ecosystem for Europe’s most critical energy infrastructure. It combines tactical AI, legal compliance, and scalable deployment to ensure long-term protection and public confidence under the Horizon Europe framework.
11. Lagrangian Optimization for Threat Neutralization & Swarm Defense
This module applies advanced Lagrangian optimization to allocate defense resources dynamically across multiple layers and prioritize intercept actions based on:
- Threat risk level (lethality, proximity, velocity)
- Resource availability (CIWS rounds, laser power, drone interceptors)
- System constraints (cooldown time, line-of-sight, EW interference)
Mathematical Model
The optimization problem is defined as:
Maximize U(x) = Σ wᵢ · Iᵢ(x) - λ · C(x)
Subject to:
Σ xᵢ ≤ R (total available resources)
xᵢ ∈ {0,1} (engage or not)
threat_priorityᵢ = f(vᵢ, dᵢ, typeᵢ, clusterᵢ)
Lagrangian:
L(x, λ) = Σ wᵢ · Iᵢ(x) - λ (Σ xᵢ - R)
Where:
wᵢ = threat weight (importance)
Iᵢ(x) = intercept success probability
λ = Lagrange multiplier representing cost per unit resource
C(x) = total cost in energy/ammo/time
R = total available intercept resources
Swarm-Aware Extension
- Identifies swarm core nodes (C2 drones, relays)
- Clustering algorithms classify drone waves by behavior
- Predictive attack trajectory matrix with reinforcement learning update
- Disruption strategies target network cohesion over brute-force engagement
Deployment
The model runs continuously in the C2-SIM layer, adjusting allocations in real time during engagements using federated AI agents. Output decisions are auditable and explainable, enabling human override if necessary.
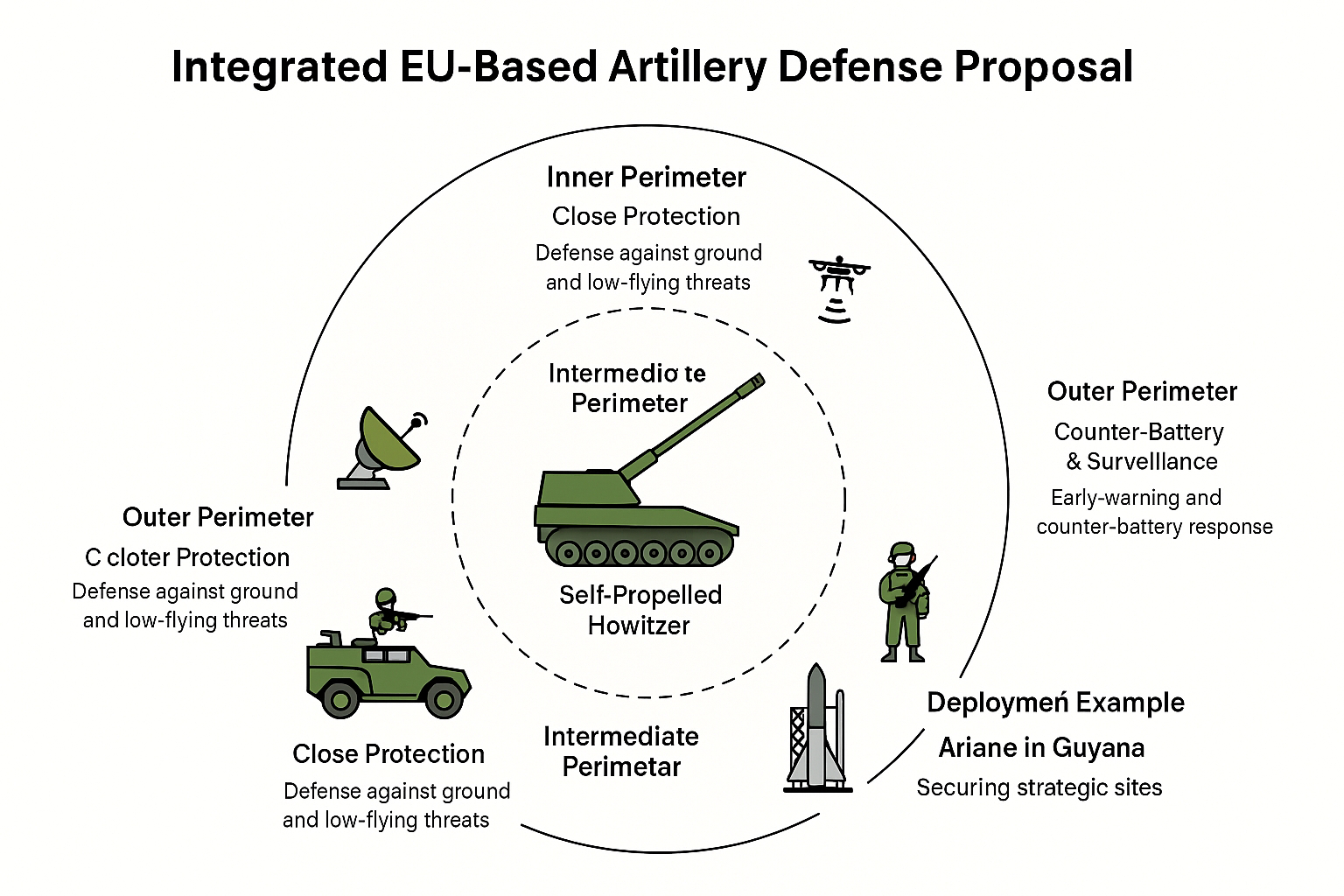
Integrated EU-Based Artillery Defense Proposal
This proposal addresses the lack of detailed artillery threat-counter components in the current infrastructure narrative. It presents a comprehensive, multi-perimeter defense concept for 360° sky and ground protection of artillery units, embedded infantry, and strategic deployments like the Ariane launch base in French Guiana.
1. Multi-Layered Defense Perimeters
A. Inner Perimeter: Close Protection
- Systems: Remote Weapon Stations (RWS) like FLW 200 mounted on GTK Boxer armored vehicles.
- Capabilities: Rapid response to close-range infantry, drones, and light vehicles.
B. Intermediate Perimeter: Air and Missile Defense
- Systems: Mobile anti-air units such as Flugabwehrkanonenpanzer Gepard or Skyranger 30.
- Capabilities: Neutralizes low-altitude aircraft, drones, and short-range missiles.
C. Outer Perimeter: Counter-Battery & Surveillance
- Systems: Radar and acoustic artillery-locating systems (e.g., COBRA radar, Artillery Command & Control).
- Capabilities: Early warning and immediate counter-battery fire.
2. Recommended Artillery Platforms & Armored Vehicles
- PzH 2000: 155mm tracked self-propelled howitzer with high firepower.
- CAESAR: 155mm wheeled system with strategic mobility.
- GTK Boxer: 8x8 modular armored vehicle (transport, fire support, command).
- ASCOD / Pizarro: Tracked infantry fighting vehicle for escorting and urban support.
3. Ballistics & Ammunition
- Standard 155mm Shells: Effective for saturation fire and support.
- Precision-Guided Munitions (e.g., BONUS, Vulcano): Accuracy against high-value or mobile targets.
European Suppliers
- Rheinmetall AG (Germany): Cannons, vehicles, ammunition.
- Nexter Systems (France): CAESAR, munitions, vehicle systems.
- Diehl Defence: Guided munitions and missile integration.
4. Use Case: Strategic Deployment in French Guiana
The Centre Spatial Guyanais (CSG) is a high-value asset protected by light infantry units like the Légion Étrangère. Its jungle surroundings and isolated location highlight the need for:
- Air-mobile infantry with rapid deployment capabilities.
- Helicopter-borne or amphibious artillery (e.g., CAESAR 6x6).
- Perimeter radar coverage and drone reconnaissance.
Conclusion: This EU-based integrated model ensures rapid response, layered defense, and scalable deployment across strategic environments. It is ideal for both continental defense and overseas missions.
EU Horizon Infrastructure & Defense Initiatives
Explore the European Union's strategic efforts in defense and infrastructure, including the ReArm Europe plan, Horizon Europe funding, and the European Defence Mechanism (EDM). Stay informed about EU's commitment to enhancing security and research infrastructures.
- ReArm Europe: Strengthening EU's defense capabilities with an €800 billion investment plan.
- Horizon Europe: The EU's key funding program for research and innovation, supporting infrastructure and defense projects.
- European Defence Mechanism (EDM): A proposed fund to facilitate joint procurement of defense equipment among EU and non-EU countries.
Tags: EU Defense, Horizon Europe, ReArm Europe, European Defence Mechanism, EU Infrastructure, Security Initiatives
Key Stakeholders
- European Commission – Horizon Europe
- EU Funding & Tenders Portal
- European Defence Agency (EDA)
- AeroSpace and Defence Industries Association of Europe (ASD)
- EARTO Working Group on Security & Defence Research
- SEREN5 – Security Research NCP Network
- Horizon Europe National Contact Points (NCP) Portal
- SESAR Joint Undertaking
- European High-Performance Computing Joint Undertaking (EuroHPC JU)
- Quantum Flagship Initiative
Disclaimer
This blog is entirely fictional and proudly biased.
If you're searching for serious and reliable information, please contact your local public servant or an official institution.
Enjoy the read – but don't take it too seriously!
BLUE SHIELD-EU: Hybrid Python/C++ Layer for AI & HPC Integration
This article presents a modular architecture for integrating AI capabilities with high-performance computing to defend European critical infrastructure, based on the BLUE SHIELD-EU initiative.
1. Architecture Overview
- Sensor Layer (C++): High-speed data acquisition from LIDAR, RADAR, etc.
- Preprocessing (C++): Normalization and filtering of raw sensor data
- AI Engine (Python/C++): PyTorch/TensorFlow + C++ backends
- Decision Module (Python): Threat prioritization and mitigation logic
- Logging/Comm Layer (C++): Secure logging and real-time system messaging
2. Key Scripts
Python: AI Inference (PyTorch)
import torch
import torchvision.models as models
model = models.resnet18(pretrained=True) model.eval()
input = torch.rand(1, 3, 224, 224) output = model(input) print("Threat score:", output)C++: Sensor Interface (simplified)
#include <iostream>
#include Python-C++ Interface with pybind11
// interface.cpp
#include # Python usage
import threat print("Score:", threat.score(1.2, 0.85))3. Timeline
| Phase | Duration | Key Activities |
|---|---|---|
| Design & Planning | 1 month | Architecture, specs |
| Module Development | 3 months | Code AI, C++ interfaces |
| Integration & Testing | 2 months | Validate end-to-end logic |
| Deployment | 1 month | Deploy + monitor |
4. Conclusion
This hybrid software layer supports real-time AI threat detection, optimal use of HPC, and EU defense system scalability. The combination of C++ and Python ensures both speed and intelligence in a modular, secure environment.
BLUE SHIELD-EU: AI-Driven 3D Defense Simulator (Python + C++ Hybrid)
Description
The BLUE SHIELD-EU simulator is a hybrid defense tool designed to simulate, detect, and respond to multi-dimensional threats targeting critical infrastructure, such as nuclear facilities. This open-source project integrates 3D visualization, real-time AI threat scoring, Lagrangian optimization, and early warning intelligence fusion.
Main Features
- 3D Threat Simulation: OpenGL + Pygame render moving objects representing threats.
- Real-Time AI Scoring: A C++ module evaluates threat proximity and movement.
- Optimization via Lagrange Multipliers: Python-based threat prioritization to maximize defense response effectiveness.
- Early Threat Detection: Fuses SIGINT, HUMINT, and IoT sensor data to preemptively assess danger.
Benefits
- Scalability: Modular structure allows integration with real defense sensors and control systems.
- Speed: Real-time scoring and visualization supports timely decisions.
- Predictive Capacity: Fusion of intelligence sources enhances early detection and proactive responses.
- Adaptability: Fully compatible with HPC environments and AI models.
Full Python Script
import pygame
import numpy as np
from scipy.optimize import minimize
import threat_ai # C++ module via pybind11
from OpenGL.GL import *
from OpenGL.GLU import *
from OpenGL.GLUT import *
import pygame.locals as pylocpygame.init() glutInit() screen = pygame.display.set_mode((800, 600), pyloc.DOUBLEBUF | pyloc.OPENGL) gluPerspective(45, (800 / 600), 0.1, 1000.0) glTranslatef(0.0, 0.0, -50) glEnable(GL_DEPTH_TEST) clock = pygame.time.Clock() running = True
class Threat: def init(self, x, y, z, vx, vy, vz, threat_level): self.x = x self.y = y self.z = z self.vx = vx self.vy = vy self.vz = vz self.threat_level = threat_level
def update(self):
self.x += self.vx
self.y += self.vy
self.z += self.vz
def draw(self):
glPushMatrix()
glTranslatef(self.x, self.y, self.z)
glColor3f(1.0, 0.0, 0.0)
glutSolidSphere(1, 12, 12)
glPopMatrix()
def optimal_response(threat_scores): n = len(threat_scores) x0 = np.ones(n) / n
def objective(x):
return -np.sum(x * threat_scores)
def constraint_eq(x):
return np.sum(x) - 1
bounds = [(0, 1) for _ in range(n)]
constraints = {'type': 'eq', 'fun': constraint_eq}
result = minimize(objective, x0, bounds=bounds, constraints=constraints)
return result.x if result.success else np.zeros(n)
def detect_early_threats(sigint, humint, iot_data): combined_score = 0.0 if sigint.get("comm_volume", 0) > 50: combined_score += 0.3 if humint.get("alert", False): combined_score += 0.4 if iot_data.get("temp_variance", 0) > 10: combined_score += 0.3 return min(combined_score, 1.0)
threats = [ Threat(-10, -10, -20, 0.2, 0.1, 0.05, 0.8), Threat(15, 5, -30, -0.1, 0.2, 0.05, 0.95) ]
while running: for event in pygame.event.get(): if event.type == pygame.QUIT: running = False
glClear(GL_COLOR_BUFFER_BIT | GL_DEPTH_BUFFER_BIT)
for threat in threats:
threat.update()
threat.draw()
positions = np.array([[t.x, t.y, t.z] for t in threats], dtype=np.float32)
scores = threat_ai.evaluate_threats(positions)
response = optimal_response(scores)
print("Response Vector:", response)
sigint = {"comm_volume": 75}
humint = {"alert": True}
iot_data = {"temp_variance": 12.5}
early_warning = detect_early_threats(sigint, humint, iot_data)
print("Early Threat Probability:", early_warning)
pygame.display.flip()
clock.tick(30)
pygame.quit()BLUE SHIELD-EU: Red & Blue Team Strategy
Red Team - Offensive Simulation
- Cyber Attacks (malware injection, AI-generated threats)
- Drone Intrusions (perimeter testing)
- GPS spoofing / signal jamming
- Social engineering (phishing, insider simulation)
Blue Team - Defense & Response
- Network monitoring and anomaly detection
- Physical security response drills
- Incident response protocols
- System patching and hardening
Bill of Materials (BOM)
| Component | Description | Estimated Cost |
|---|---|---|
| Raspberry Pi 5 / Jetson Nano | Edge computing & sensor nodes | €80 x 20 = €1,600 |
| Industrial-grade drones | Intrusion simulation and airspace testing | €1,500 x 5 = €7,500 |
| Firewall & IDS appliances | Defense and traffic inspection | €10,000 |
| High-res surveillance cameras | Perimeter monitoring | €500 x 10 = €5,000 |
| Simulation Server Cluster | Digital twins and AI-based training | €15,000 |
Human Resources per Team
Red Team
- 1 Cybersecurity Lead
- 2 Ethical Hackers
- 1 UAV Operator
- 1 Social Engineering Specialist
Blue Team
- 1 Network Security Analyst
- 1 Incident Response Manager
- 1 Physical Security Specialist
- 1 System Administrator
- 1 AI/Data Engineer
Estimated Monthly Cost (Human Resources)
| Role | Cost/Month | Team |
|---|---|---|
| Cybersecurity Lead | €6,000 | Red |
| Ethical Hacker x2 | €5,000 x 2 = €10,000 | Red |
| UAV Operator | €4,000 | Red |
| Social Engineering Expert | €4,500 | Red |
| Network Analyst | €5,000 | Blue |
| Incident Manager | €5,500 | Blue |
| Physical Security | €3,500 | Blue |
| System Admin | €4,000 | Blue |
| AI/Data Engineer | €6,000 | Blue |
Automation Proposals
- Automated vulnerability scanning (weekly with AI-adjusted rule sets)
- Red Team bot to simulate phishing, intrusion & DoS randomly across network (configurable)
- Blue Team AI assistant to analyze logs and suggest responses in real time
- Digital twin environments with continuous threat injection & feedback loop
Assessment Automation
- Real-time scoring of Red/Blue performance based on SLA deviation, MTTR, breach depth
- Dashboard visualization of readiness index over time
- Simulated tabletop wargaming scenarios for strategic decision testing
EU Horizon: Critical Infrastructure Vulnerabilities and Russian Intelligence Threats
The European Union’s critical infrastructure faces complex threats from Russian state actors such as the GRU and FSB, as well as from affiliated mercenaries and organized criminal networks.
Main Vulnerabilities That May Be Exploited
1. Cyber Infrastructure
- GRU Unit 29155 has been linked to cyberattacks targeting government services, financial systems, and power grids across NATO countries. [Source]
- FSB operations have led extensive hacking campaigns against public officials and institutions.
- Russian cyber actors continue to exploit known vulnerabilities in global critical systems. [Source: CISA]
2. Physical Infrastructure
- Sabotage and arson attacks targeting hospitals and commercial centers have been linked to Russian military intelligence. [Source]
- Undersea internet cables are being mapped by Russian submarines, putting global communication systems at risk. [Source]
3. Hybrid Threats and Criminal Alliances
- Organized criminal gangs serve as proxies for Russian state actors, executing cyberattacks, sabotage operations, and data theft.
- AI-driven disinformation and cognitive warfare tactics are used to manipulate public opinion and destabilize societies. [Read more]
Countermeasures and Strategic Responses
1. Regulatory and Policy Frameworks
- The EU’s ProtectEU Strategy reinforces internal security and resilience against hybrid threats. [Source]
- The CER and NIS2 Directives aim to strengthen essential services and infrastructure protections.
2. Strengthening Cybersecurity
- Launch of AI labs and security alliances to counter advanced cyber threats.
- Digital literacy campaigns to reduce the impact of disinformation and raise awareness.
3. International Cooperation and Intelligence Sharing
- EU-wide collaboration to exchange threat intelligence and respond to coordinated attacks.
- Partnership with Europol to monitor and dismantle criminal networks acting on behalf of foreign entities.
Strategic Recommendations
- Invest in resilience: modernize and secure critical infrastructure (energy, telecom, transportation).
- Public-private partnerships to enhance detection and response capacity.
- Real-time monitoring systems to detect and mitigate cyber threats proactively.
- Training and education for both professionals and the general public to counter hybrid threats.
By adopting a comprehensive and collaborative approach, the EU can bolster its resilience and mitigate the evolving threats posed by state and non-state actors.
EU Horizon: Swarm Drone Saturation Simulation
Overview
This simulation models swarm drone saturation using a conceptual adaptation of Gauss's Theorem. Drones approach a defensive perimeter and the system calculates the flux (number entering) and the divergence (accumulation within).
Live Simulation
The canvas below visualizes the simulation in real-time. Red dots represent drones, and the blue dashed circle indicates the defensive perimeter. The heatmap tracks density zones.
Key Metrics
Flux (entries): 0
Drones Inside: 0
Saturation Level: 0.00
Conceptual Background
Gauss's Theorem relates the flux of a field through a surface to the divergence within a volume. Here, drones represent vector fields entering a protected domain. The flux gives insight into defense overload, and divergence indicates internal pressure buildup. This visual protection scenario helps analyze infrastructure breach probabilities under coordinated drone swarms.
Further Development
- Add reinforcement learning for defense prediction
- Model radar interference and adaptive jamming
- Simulate multi-layered defense strategies
Simulation Overview
This script implements an interactive simulation of a swarm drone saturation attack modeled conceptually using Gauss's Theorem. Below is a summary of its main components:
Drone Initialization
100 drones are randomly generated outside a defensive circle. Each drone is assigned a velocity vector directed toward the center.
Live Simulation
Drones move frame by frame toward the defensive perimeter. Their positions are updated in real-time using a p5.js canvas.
Flux and Saturation Metrics
- Flux: Counts how many drones have crossed into the defensive perimeter.
- Inside Count: Tracks the number of drones currently within the perimeter.
- Saturation Level: Ratio of drones inside to the total number of drones.
Heatmap Canvas
A secondary canvas displays a density heatmap based on drone positions, highlighting saturation zones over time.
Export Function
A button allows users to export the current simulation metrics (flux, insideCount, saturationLevel) as a downloadable .json file.
Overall, this simulation is designed as a conceptual and visual tool to explore swarm drone behavior, perimeter penetration, and the estimation of defensive load capacity. Industries, Technologies and Certified Suppliers for EU Horizon Infrastructure & Defense Tenders
To respond effectively to the scenarios envisioned under the EU Horizon 2025 program in the areas of infrastructure and defense, it's crucial to identify the key industries, workshops, technologies and potential local EU-based suppliers that would play a role in project execution.
Key Industries Involved
- Aerospace and Defense Manufacturing – for drones, surveillance, communication systems, armored vehicles, etc.
- Cybersecurity & Digital Infrastructure – secure networks, data centers, digital sovereignty, AI systems.
- Green Construction & Civil Engineering – smart bases, resilient energy infrastructures, military housing, logistics hubs.
- Telecommunications & Satellite Systems – encrypted communication, GNSS, secure mobile networks.
- Industrial Automation & Robotics – autonomous logistics, warehouse automation, defense robots.
- Energy & Power Systems – portable renewable energy, battlefield energy storage, microgrids.
- Advanced Materials & Additive Manufacturing – ballistic composites, 3D printing, lightweight armor.
- Transport & Mobility Technologies – military-grade electric vehicles, rail & port dual-use infrastructure.
Typical Workshops & Technical Partners
- Precision metalworking & welding facilities
- PCB manufacturing & embedded systems labs
- Composite materials workshops
- Automation & control engineering firms
- Certified R&D labs for military-grade testing
- Small-scale fabrication and prototyping units
- Defense-grade electronics assembly workshops
Potential EU-Based Suppliers & Partners
- Leonardo S.p.A (Italy) – Aerospace, defense systems
- Thales Group (France) – Cybersecurity, defense electronics
- Indra Sistemas (Spain) – Command and control systems
- Rheinmetall AG (Germany) – Armored vehicles, munitions
- Saab AB (Sweden) – Naval and air systems
- Airbus Defence and Space (EU-wide) – Satellites, UAVs
- Fraunhofer Institutes (Germany) – Applied research and prototyping
- Fincantieri (Italy) – Naval shipyards, dual-use maritime systems
- Local SMEs and startups through EU clusters such as EDA’s PADR, EIT Manufacturing, or DIHs (Digital Innovation Hubs)
Certified Site Construction Facilities and Concrete Suppliers
France
- VINCI – Global construction and infrastructure projects
- Eiffage – Public works, civil and industrial engineering
- Heidelberg Materials France – Concrete and aggregates
- CRH France – Cement and concrete products
- QUALIBAT – Construction company certification authority
Switzerland
- Holcim – Cement, concrete, and sustainable construction
- CRH Switzerland – Aggregates and cement solutions
- Swiss Safety Center – Certification and compliance services
- SGS Switzerland – Testing and certification across industries
HVAC, Electrical, Electronics, Automation & Ventilation Requirements
High-performance military and dual-use infrastructure requires integration of resilient, energy-efficient and smart systems for climate control, power management, data processing and automation. Below is a breakdown of the essential components and certified European suppliers.
Core Technical Requirements
- HVAC systems for operational bases, data centers, and mobile units
- Electrical distribution & smart grids with load balancing and backup systems
- Industrial automation & PLC integration for remote monitoring and process control
- Electronics & embedded systems for sensors, security and command units
- Advanced ventilation systems for NBC (nuclear, biological, chemical) protection and air quality control
Recommended Suppliers & Integrators (France, EU, Switzerland)
France
- Schneider Electric – Electrical automation, energy distribution, smart infrastructure
- Legrand – Data and electrical systems for secure facilities
- Daikin France – Certified HVAC solutions including VRV/VRF
- Sauter France – Building automation systems
- Aldes – Air purification, HRV, and indoor air quality
Switzerland
- Stäfa Control System – BMS and HVAC automation
- Huber+Suhner – Fiber optics, RF and power components
- Belimo – HVAC actuators and control valves
- Siemens Switzerland – Smart grids, HVAC control, energy automation
EU-Wide
- Bosch Industrial – Industrial energy systems and HVAC
- Phoenix Contact – I/O, PLCs, cybersecurity and automation
- ABB Group – Robotics, drives, power electronics
- Helvar – Lighting control and building automation
- NIBE – Sustainable HVAC systems for dual-use installations
Compliance & Certification Tips
- Ensure compliance with EN 15232 (energy performance of building automation)
- Use systems compatible with Modbus, BACnet, KNX for open integration
- Request CE, ISO 9001, ISO 14001, and AQAP where applicable
Recommendations for Respondents
- Build consortia with both large defense primes and innovative SMEs
- Leverage European Digital Innovation Hubs (EDIHs) and local clusters
- Prepare for dual-use certification and compliance with EU defense regulations
- Focus on cyber-resilience, open-source alternatives, and strategic autonomy
This roadmap ensures readiness to meet EU funding calls while enhancing continental strategic autonomy in the face of modern hybrid threats and infrastructure challenges.
Industries, Technologies and Certified Suppliers for EU Horizon Infrastructure & Defense Tenders
To respond effectively to the scenarios envisioned under the EU Horizon 2025 program in the areas of infrastructure and defense, it's crucial to identify the key industries, workshops, technologies and potential local EU-based suppliers that would play a role in project execution.
Key Industries Involved
- Aerospace and Defense Manufacturing
- Cybersecurity & Digital Infrastructure
- Green Construction & Civil Engineering
- Telecommunications & Satellite Systems
- Industrial Automation & Robotics
- Energy & Power Systems
- Advanced Materials & Additive Manufacturing
- Transport & Mobility Technologies
Typical Workshops & Technical Partners
- Precision metalworking & welding
- PCB manufacturing & embedded systems
- Composite materials workshops
- Automation & control engineering
- Certified military R&D labs
- Small-batch fabrication units
Certified EU-Based Suppliers
- Leonardo (Italy)
- Thales Group (France)
- Indra Sistemas (Spain)
- Rheinmetall AG (Germany)
- Saab AB (Sweden)
- Airbus Defence (EU)
- Fraunhofer Institutes (Germany)
- Fincantieri (Italy)
Certified Construction & Concrete Facilities
France
Switzerland
HVAC, Electrical, Automation & Ventilation
- Schneider Electric (France)
- Legrand (France)
- Daikin France
- Sauter France
- Aldes
- Stäfa Control System (CH)
- Huber+Suhner (CH)
- Belimo (CH)
- Siemens Switzerland
- Bosch Industrial
- Phoenix Contact
- ABB Group
- Helvar (Finland)
- NIBE
Compliance Tips
- EN 15232 for BMS/HVAC energy efficiency
- Protocols: Modbus, BACnet, KNX
- Certifications: CE, ISO 9001/14001, AQAP
Strategic Recommendations
- Form consortia with certified defense primes + SMEs
- Use EDIHs and European clusters
- Focus on cyber resilience and sovereignty
This roadmap ensures compliance, scalability and strategic readiness across defense and infrastructure projects under Horizon Europe.
Concrete Adaptation for Nuclear and Military Applications
Nuclear power plants and military bunkers require specialized construction techniques. Concrete used in these facilities must resist radiation, extreme pressure, and long-term environmental damage. This article summarizes the key materials and engineering features used in such high-security installations.
1. High-Density and Shielding Concrete
To protect from gamma and neutron radiation, engineers use high-density concrete with barite, magnetite, or serpentine. These aggregates increase shielding capacity far beyond conventional mixes.
2. Blast and Seismic Resistance
Military-grade infrastructure often includes ultra-high performance concrete (UHPC), which provides compressive strength above 150 MPa and can withstand extreme thermal shocks or blasts.
3. Smart and Durable Materials
Innovations such as self-healing concrete and fiber-reinforced blends ensure long-term reliability and reduce the need for maintenance even under hostile conditions.
4. Secure Production and Certification
These materials are often mixed on-site using mobile batching systems integrated with SCADA and IoT. Quality control complies with IAEA, NATO, and national military standards.
From nuclear reactors to underground command bunkers, concrete evolves to meet critical demands of safety, endurance, and protection.
Threat Assessment: BLUE SHIELD-EU Under Hybrid Hostile Targeting
The BLUE SHIELD-EU initiative, as described in the EU Horizon Infrastructure Defense program, is a cutting-edge modular system designed to protect Europe’s strategic and nuclear infrastructure through AI-powered swarm defense, SIGINT/IMINT fusion, and cyber-electronic warfare hardening.
Its relevance makes it a high-value target for hybrid attacks from hostile actors, notably Russian intelligence agencies (FSB, GRU) and affiliated mercenary groups (e.g., Wagner proxies). Below is a structured threat scenario, including potential exploits, vulnerabilities, and recommended countermeasures.
1. Threat Scenarios Involving FSB/GRU and Proxies
- Cyber Espionage (GRU/Sandworm): Targeting SCADA/ICS systems, AI optimization layers, and introducing logic bombs into digital twin simulations via firmware implants or phishing.
- Insider Threat (FSB HUMINT): Recruitment or coercion of personnel within subcontractors or EU institutions.
- Drone/EW Sabotage (Proxies): Low-cost drone swarms with decoy payloads to overload AI defense and breach perimeter systems.
- Disinformation Warfare: State-sponsored media campaigns to frame the project as a NATO-controlled "AI war machine", eroding support.
- Supply Chain Disruption: Physical or digital attacks on hardware logistics (GPU/FPGA shipments) or manufacturing hubs.
2. Security Breaches, Vulnerabilities & Exploits
Known Breach Vectors:
- Firmware Supply Chain Breach: Infected microchips in AI modules enabling persistent remote access.
- AI Model Poisoning: Feeding crafted adversarial data to manipulate AI threat assessment outputs.
- Credential Dumping & Lateral Movement: Using tools like Mimikatz or Cobalt Strike to escalate privileges inside hybrid OT/IT environments.
Critical Vulnerabilities:
| Type | Vulnerability | CVE / Exploit | Threat Usage |
|---|---|---|---|
| SCADA/ICS | Modbus TCP no authentication | CVE-2019-6826 | False sensor commands |
| AI Hardware | NVIDIA Jetson Buffer Overflow | CVE-2022-28181 | Remote code injection |
| Networking | Unsecured SNMP v2 | CVE-2020-15857 | Network mapping & DoS |
| OpenPLC Web UI | Command Injection | CVE-2021-22681 | System reconfiguration |
| Windows/Linux | SMBv1 exploit | MS17-010 (EternalBlue) | Worm propagation & lateral access |
Notable Exploits:
- Remote Code Execution: Via insecure REST APIs or exposed simulators.
- AI Blind Spot Injection: Adversarial LIDAR/IR perturbation to bypass detection layers.
- Command & Control Hijacking: Proxy implants redirecting AI logic through rogue nodes.
3. Advanced Countermeasures
Cybersecurity & Infrastructure Defense:
- Air-gapped fallback SCADA with forensic rollback capabilities.
- AI-based intrusion detection at firmware and model levels.
- Zero-trust segmentation of OT/IT environments and encrypted PLC communication.
Human Security & Insider Defense:
- Behavioral monitoring AI trained on insider threat patterns.
- Ghost HR positions to test HUMINT attempts in critical roles.
- Contractor cross-validation with NATO/EU security registries.
Drone & EW Protection:
- Low-IR mode CIWS with drone-hunter AI defense routines.
- Hardened RF architecture and spectrum camouflage protocols.
Strategic Communication Warfare:
- Deployment of verified influencers and OSINT partners to counteract hostile narratives.
- Interactive dashboards, VR tours and transparency nodes for public trust.
Operational Logistics & Physical Security:
- Smart convoys with randomized routes and geo-fenced maritime access.
- AI-enhanced liaison networks to detect potential sabotage patterns on-site.
Conclusion:
As the EU scales up BLUE SHIELD-EU, it must anticipate hostile state actors deploying asymmetric tactics, cyber exploits, and narrative warfare. This multilayered threat landscape requires an integrated counterintelligence architecture combining cybersecurity, physical resilience, behavioral AI, and information dominance.
Disclaimer:
The reproduction, distribution, or use of this content is not permitted without the explicit written permission of the author.
Recommended Workshops Near the Gravelines Nuclear Plant
As part of the EU Horizon Infrastructure Defense initiative and the upcoming deployment of the BLUE SHIELD-EU system at the Gravelines Nuclear Power Plant, the following workshops are strategically recommended to support manufacturing, electronics, and rapid response systems.
1. Advanced CNC Machining & Precision Fabrication Workshop
This facility should focus on producing high-precision components for defense and control systems, including:
- Sensor enclosures (Jetson, Movidius)
- LIDAR and RADAR mounts
- EMP-shielded control system cases
Key skills: blueprint reading, CNC lathe/mill operation, precision metrology.
2. Additive Manufacturing and Materials Lab
This lab will produce lightweight and durable components using metal and polymer 3D printing. Applications include:
- Drone and sensor structures
- Rapid prototyping of housings
- Custom firefighting UAV parts
Includes AI-driven part inspection for quality and reliability.
3. PCB Fabrication & Electronics Assembly Facility
Essential for building IoT and AI-based security modules:
- Surface Mount Technology (SMT) assembly
- Shielded PCBs for mission-critical systems
- Secure electronics for automated defense tools
Compliant with industrial cybersecurity standards.
4. Non-Destructive Testing (NDT) & Quality Assurance Center
To ensure reliability of critical parts, this center would use:
- Ultrasonic and radiographic testing
- Magnetic particle inspection
- High-stress component analysis for nuclear-grade systems
5. AI & Cybersecurity Simulation Hub
This hub would support the development and validation of AI defense algorithms and secure industrial control systems:
- Simulations of cyber-physical attacks
- AI training for SCADA threat detection
- Digital twin deployment for emergency readiness
6. Emergency Response Training Center (AR/VR)
Equipped with immersive technologies to train defense personnel in:
- Augmented reality emergency scenarios
- Firefighting drone operations
- Coordinated disaster response with first responders
Strategic Benefits
Gravelines is close to Dunkirk and benefits from an industrial ecosystem ideal for such workshops. These installations would contribute to:
- European defense resilience
- Technological sovereignty
- Local economic development
Relevant EU Initiatives: EASI-STRESS | Dunkerque Energie Creative
Prepared by RK – Tech Policy, Defense & Innovation
OSINT Disclaimer
This OSINT (Open-Source Intelligence) exercise is conducted strictly for educational and training purposes. All data collected and analyzed originates from publicly available sources. No attempt will be made to access private, restricted, or classified information. The exercise respects all applicable laws, ethical guidelines, and terms of service of the platforms involved.
Participants are reminded that any use of this information outside the intended educational context is strictly prohibited and may be subject to legal consequences.
Relevant EU Legal Framework:
- EU General Data Protection Regulation (GDPR) – Regulation (EU) 2016/679
- Charter of Fundamental Rights of the European Union – Article 8: Protection of personal data
- Directive on security of network and information systems (NIS2) – Directive (EU) 2022/2555
- Directive on privacy and electronic communications (ePrivacy Directive) – Directive 2002/58/EC
- European Convention on Human Rights – Article 8: Right to respect for private and family life
Potential Stakeholders for Workshops Near the Gravelines Nuclear Plant
As part of the EU Horizon initiative to reinforce defense-related infrastructure, the following organizations and stakeholders are key to establishing industrial workshops and innovation hubs near the Gravelines Nuclear Power Plant.
- European Commission - Horizon Europe
- European Parliament - Subcommittee on Security and Defence
- CEA - French Alternative Energies and Atomic Energy Commission
- EDF (Électricité de France)
- ANSES - French Agency for Food, Environmental and Occupational Health & Safety
- Ministère des Armées (French Ministry of Armed Forces)
- EURATOM - European Atomic Energy Community
- ENISA - European Union Agency for Cybersecurity
- Thales Group
- Airbus Defence and Space
- Leonardo S.p.A.
- NATO - Science and Technology Organization
- INRIA - French National Institute for Research in Digital Science and Technology
- Arts et Métiers Institute of Technology
- Canadian Institute for Military and Veteran Health Research (for dual-nation R&D)
Scaling EU Critical Infrastructure & Defense Initiatives
The EU faces growing challenges in safeguarding its critical infrastructures—both physical and digital. As part of the Horizon Europe and European Defence Fund strategic vision, scalable, modular, and interoperable infrastructure systems are essential to ensure resilience, autonomy, and joint readiness across all EU27 Member States.
1. Multi-Sector Critical Infrastructure Resilience
- Energy: Smart grids, nuclear safety, distributed renewables with embedded cybersecurity.
- Water: Real-time water quality monitoring, contamination response units.
- Transport: Protected multimodal corridors, autonomous & secure logistics platforms.
- Health: Resilient health cloud, mobile surgical units, and dual-use facilities.
- Cloud & Data: EU-native digital sovereignty platforms like GAIA-X.
2. Federated Architecture & Interoperability
Using a modular and federated approach allows each country to deploy its infrastructure layer while maintaining full interoperability at the European level. Core components:
- Standardized APIs and protocols
- AI-enhanced Edge Nodes
- ERP/SCADA integration with platforms like Odoo
3. Cyber-Physical Resilience & Simulation Layers
Cybersecurity must be native. Scaling must embed:
- Quantum-resistant cryptography
- AI-driven anomaly detection
- Zero Trust architecture
- Real-time attack simulation sandboxes
4. Replicability & Local Adaptation
Each infrastructure package (InfraKit) must be adaptable to local needs but fully EU-compliant. Examples:
- Translated protocols & risk assessment dashboards
- Policy toolkits aligned with NIS2, GDPR, and Green Deal
5. Integration with EU Funding Instruments
Projects must align with:
- Horizon Europe Cluster 3 (Security)
- European Defence Fund (EDF) dual-use projects
- Cross-border public-private consortia
6. The Role of the European Education and Professional Framework
One of the most powerful levers to ensure long-term civil-military readiness is the standardization of professional education and lifelong training across the EU.
- Establishing dual-career tracks for civilian professionals trained in emergency operations, logistics, cyber-defense, and critical asset management.
- Creating certified EU-wide profiles aligned with EQF (European Qualifications Framework) for operational roles, capable of rapid deployment and coordination with NATO or EU CSDP missions.
- Supporting lifelong learning modules through digital platforms and in-person academies to ensure resilience, upskilling, and interoperability in crisis scenarios.
7. Pedagogy for Social Engagement & EU Security Commitment
A long-term secure Europe requires not only technology and professionals but also a committed and informed society. This calls for a pedagogical model that fosters civic responsibility and EU-level security awareness among citizens, students, and workers alike.
- Embed security and resilience literacy into primary, secondary and higher education curricula.
- Promote European values of solidarity, coordination, and peacebuilding through interactive learning formats and media.
- Launch participatory simulations and digital platforms to engage young people in EU civil defense, disaster response, and cyber-protection scenarios.
- Create community resilience networks linked to municipal, national, and EU systems, empowering citizens to act as first responders.
Education is the bridge between strategy and society. By building a pedagogical culture of engagement, the EU ensures both legitimacy and effectiveness of its security policy and long-term infrastructure resilience.
8. Digital Twin & Visual Simulation
Each infrastructure project should include a digital twin, allowing:
- Stress testing scenarios (climate, sabotage, war)
- Training AI agents and human operators together
- Visual dashboards built with Unity, Unreal or Pygame
9. Governance, Ethics & Legal Integration
- Embed legal protocols for emergency operations
- Ensure ethics-by-design in AI systems and surveillance
- Enable structured public-private collaborations
Conclusion
The EU must invest not only in physical infrastructures but also in people, pedagogy, and simulation systems. Civilian and military readiness must converge through common standards, interoperable platforms, and a shared doctrine of strategic resilience.
This proposal is open to feedback and collaborative expansion. Let’s build the infrastructure of a sovereign, prepared, and connected Europe.
10. Key EU Stakeholders & Networks
To scale and operationalize this vision, collaboration with EU-level institutions, agencies, and networks is essential. Below is a curated list of stakeholders relevant to infrastructure, defense, education, cybersecurity, and civil protection:
- European Defence Fund (EDF) – Funds dual-use and defense innovation projects.
- Horizon Europe – The EU’s main R&D program, supporting infrastructure and security projects.
- European Defence Agency (EDA) – Coordinates defense capability development and research across Member States.
- European Commission – Main executive body supporting strategic resilience and policy integration.
- European External Action Service (EEAS) – EU’s diplomatic and security policy service.
- EUROPOL – Provides criminal intelligence and cybercrime cooperation.
- ENISA – EU Cybersecurity Agency – Develops standards, training, and risk frameworks.
- EUROJUST – Enhances cross-border judicial cooperation, especially in cyber and terrorism cases.
- EACEA – Education, Audiovisual and Culture Executive Agency – Manages Erasmus+, Creative Europe and lifelong learning programs.
- EU Solidarity Fund (EUSF) – Provides rapid assistance during major natural disasters.
- EU Civil Protection Mechanism (UCPM) – Coordinates disaster preparedness and emergency response.
- Pact for Skills – European Commission – Supports professional training and upskilling for critical sectors.
- European Youth Portal – Engages young citizens in EU policy, volunteering, and resilience efforts.
- JOINUP – Open source and interoperability hub for digital public services.
- EU Open Data Portal – Essential for simulation, risk modeling, and AI training datasets.
Comprehensive Model for Optimizing Public Transport Supply and Demand in EU-27
EU Horizon Strategy: Wartime Medical SUPPLY: Resilience and Innovation
SISO Principle in EU Infrastructure and Defense: Technical Deep Dive
What is SISO? The Principle and Its Relevance
The Single Input, Single Output (SISO) principle comes from systems engineering and control theory. In a SISO system, a single input directly determines a single output. This structure is prized for its transparency, auditability, and ease of traceability. However, in the context of EU infrastructure, defense, and digital autonomy, SISO also introduces unique risks that demand careful management.
SISO: “Shit In, Shit Out”—Why Input Quality Can’t Be Ignored
The SISO principle is sometimes bluntly summarized as “Shit In, Shit Out”. No matter how advanced your system, if the data you put in is flawed, the output will be too. In EU critical infrastructure and defense:
- Bad Data = Bad Decisions: If a sensor is misconfigured or a data feed is corrupted, even the most sophisticated defense system can fail—or become dangerous.
- No Shortcuts in Validation: SISO means every input, whether human or machine, must be strictly validated and sourced from trusted channels.
- Building Trustworthy Systems: The lesson is clear: investing in the quality and verification of your data inputs is as important as the technology itself. Trustworthy infrastructure starts at the source.
As the EU drives strategic autonomy and resilience, the SISO rule—your system is only as good as your inputs—remains mission critical.
Technical Deep Dive: Risks, Threats, and Contingencies
1. SISO and Vulnerability Exposure
While SISO’s direct input-output mapping makes for simple, auditable systems, it also creates a single point of vulnerability:
- Data Injection Attacks: A compromised sensor or command input leads directly to potentially unsafe or unintended actions.
- Lack of Redundancy: If an input fails or is manipulated, the output is immediately affected—potentially leading to service denial, safety risks, or system shutdowns.
Example: In a European border surveillance network, a single motion sensor triggers an automated gate closure. If an attacker spoofs the sensor, the system might seal the gate at the wrong time, disrupting legitimate movement or allowing undetected entry.
2. Threat Vectors in EU Infrastructure
-
Supply Chain Contamination:
A utility provider sources smart grid controllers externally. If one is compromised at the factory, a rogue input (like a faked overload) could prompt SISO logic to trigger a blackout segment.
Real case: During the 2022 EU grid stress tests, supply chain issues were found in SISO-based automation. -
Insider Threats:
An IT administrator in a transport authority with system access inputs an unauthorized command. SISO logic may reroute trains onto the wrong track, without any cross-checks.
Real case: EU railway incidents have been traced to single-step actuation logic exploited by operator error or sabotage. -
Spoofing and Data Manipulation:
Attackers access a legacy SCADA network and inject false water-level readings. The SISO system, trusting the input, may open or close floodgates at the wrong time, risking downstream flooding.
Real case: EU urban resilience drills highlighted this vulnerability in SISO-based flood defense systems.
3. Risk Amplification in Critical Systems
-
False Positives/Negatives:
A drone defense system at a major EU port receives a spoofed radar ping and launches a counter-drone, risking false alarms or even collateral damage.
Horizon-funded MARITIME SHIELD recommended dual-channel validation for critical actuators after finding SISO vulnerabilities. -
Cascading Effects:
A malformed configuration file in a telecom exchange (triggered by a SISO event) leads to hours of lost connectivity, showing how one bad input can propagate widely.
4. Contingency Strategies for SISO Risks
- Input Validation and Authentication: All inputs (sensor, human, or device) should be cryptographically signed and verified. For example, EU border security mandates authentication for sensor and camera data before SISO logic is applied.
- Monitoring and Anomaly Detection: AI-driven systems like those in the Horizon Europe SECUREGRID project flag unexpected SISO input patterns before they cause harm.
- Fallback and Redundancy Protocols: For critical pathways (e.g., air traffic control), secondary data feeds and human verification can halt automated SISO actions when suspicious inputs are detected.
- Penetration Testing and Forensics: EU policy increasingly requires red-team tests on input channels and comprehensive event logging to trace and analyze any incident rapidly.
Conclusion: SISO in the Threat Landscape
SISO logic enables transparency, auditability, and regulatory compliance—but it also amplifies the risks of bad data and single-point failure. Real-world incidents across the EU illustrate both the power and vulnerability of this model. As Europe builds toward digital and defense autonomy, the quality, verification, and monitoring of every input must remain at the core of resilient, future-proof infrastructure.
Index Summary
- 1. Introduction
- 2. Horizon Europe and Infrastructure Development
- 3. Defense Innovation in the EU
- 4. Public-Private Collaboration Models
- 5. Case Studies and Success Stories
- 6. Future Challenges and Opportunities
- 7. Conclusion
- 8. References & Further Reading
Jump to any section above for a focused read.
Relevant EU Defence Funds and Strategies
-
European Defence Fund (EDF):
The primary EU funding tool for collaborative defence R&D and industrial projects, with a budget of €7.3 billion (2021–2027). Open to companies, SMEs, research centers, and consortia (at least 3 entities from 3 EU countries) for projects in land, air, naval, cyber, space, and energy. -
Act in Support of Ammunition Production (ASAP):
Targeted grants to scale up EU ammunition and explosives manufacturing, modernize facilities, and strengthen supply chains—ideal for manufacturers and partners in the defence sector. -
European Defence Industry Reinforcement through Common Procurement Act (EDIRPA):
Supports joint procurement by EU member states and industry groups (consortia from at least 2 countries), co-financing urgent or strategic defence purchases. -
European Defence Industrial Strategy (EDIS) & European Defence Industry Programme (EDIP):
EDIS, launched in 2024, provides a comprehensive roadmap to strengthen Europe's defence base, increase technological sovereignty, and boost resilience. EDIP (planned €1.5 billion) will fund next-generation defence technologies and support innovative projects. -
Security Action For Europe (SAFE) Fund (proposed):
An ambitious initiative aiming to mobilize up to €150 billion for reinforcing the entire European defence sector, infrastructure, and capabilities. Details and calls for projects will be announced as the fund develops.
Strategic Perspective:
The new European Defence Industrial Strategy (EDIS) aligns all these funding instruments toward a common vision: making Europe more self-reliant, innovative, and responsive to new security challenges. The scenario described above—where the EU increases its defence funding and industrial support—offers major benefits:
- Accelerated innovation and growth for companies, SMEs, and research institutions working on defence technologies.
- Opportunities for cross-border collaboration, allowing businesses to form strategic alliances and enter new markets.
- Enhanced industrial resilience and capacity, especially in critical domains like ammunition, AI, space, and cyber.
- Access to stable, long-term funding to support large-scale projects and infrastructure upgrades.
- Improved ability to respond to geopolitical risks and reduce dependency on non-EU suppliers.
Chapter VI: Adapting the BLUE SHIELD-EU Framework to GCC Oil Refineries and Extraction Fields
The EU Horizon Infrastructure Defense initiative, notably the BLUE SHIELD-EU framework, was originally conceived to safeguard European nuclear facilities. However, this model can be strategically adapted to protect critical oil and gas infrastructure in the Gulf Cooperation Council (GCC) region—home to some of the world’s largest refining and extraction facilities.
Core Components of the BLUE SHIELD-EU Model
- Smart Sensor Networks: Real-time perimeter and internal monitoring
- AI-Based Surveillance: Predictive analytics and automated threat recognition
- Cybersecurity Architecture: Network segmentation, intrusion detection, and real-time response
- Anti-Drone Systems: Radar detection and mitigation capabilities
- Integrated Emergency Response: Coordination with fire, medical, and military units
Application to GCC Energy Infrastructure
The following GCC facilities are priority candidates for application of the adapted framework:
| Facility | Location | Operator | Recommended Security Focus |
|---|---|---|---|
| Ruwais Refinery | UAE | ADNOC | AI surveillance & cybersecurity upgrades |
| Al Zour Refinery | Kuwait | KIPIC | Drone defense & emergency protocols |
| Ras Tanura Refinery | Saudi Arabia | Saudi Aramco | Threat mapping & perimeter sensors |
| Ghawar Oil Field | Saudi Arabia | Saudi Aramco | Operational AI & predictive maintenance |
Strategic Steps for Implementation
- Conduct Risk Assessment: Evaluate physical, cyber, and environmental vulnerabilities.
- Deploy Modular Sensor Systems: Integrate with SCADA and operational control rooms.
- Embed AI Surveillance: Enable anomaly detection and intelligent response.
- Integrate Anti-Drone Measures: Use radar and RF jamming technologies.
- Establish Crisis Protocols: Simulations with civil defense and emergency services.
Compliance and Cooperation
To ensure success, adaptation should comply with local laws and environmental standards, while promoting international cooperation. Stakeholders from security, energy, and government sectors must be engaged from the design phase. Regular audits, drills, and threat intelligence sharing are essential components of sustainable protection.
This chapter highlights how defense innovation from the European Horizon framework can be exported and scaled to protect strategic energy assets beyond nuclear infrastructure—laying a foundation for global resilience and energy security.
Public Stakeholders in GCC Oil and Energy Security
| Organization | Country | Description |
|---|---|---|
| ADNOC | UAE | Manages Ruwais Refinery and UAE’s oil and gas value chain. |
| KIPIC | Kuwait | Operator of Al Zour Refinery and petrochemical facilities. |
| Saudi Aramco | Saudi Arabia | World’s largest oil producer, manages Ghawar and Ras Tanura. |
| OQ | Oman | Omani state energy company and Duqm Refinery co-operator. |
| QatarEnergy | Qatar | Qatar’s state-owned firm, active in LNG and upstream security. |
| BAPCO | Bahrain | Operates Sitra Refinery and national distribution networks. |
| Ministry of Interior – KSA | Saudi Arabia | Handles industrial protection and critical site response. |
| CICPA | UAE | Protects UAE's critical coastal and energy infrastructure. |
| UAE Cybersecurity Council / GISEC | UAE | Coordinates national cyber defense across energy sectors. |
Private and Joint-Venture Stakeholders
| Company | Country / Region | Description |
|---|---|---|
| TotalEnergies | France / KSA | Operates the SATORP JV refinery in Saudi Arabia with Aramco. |
| OQ8 (OQ + KPI) | Oman / Kuwait | JV managing the Duqm Refinery; combines OQ and Kuwait Petroleum Intl. |
| Lockheed Martin | USA / GCC | Provides advanced monitoring, drone defense and AI for refineries. |
| EDGE Group | UAE | Defense tech provider; involved in cyber, drones, and infrastructure protection. |
| Honeywell | USA / GCC | Supplies SCADA and refinery automation systems across GCC refineries. |
| Siemens Energy | Germany / GCC | Automation, grid security, and AI predictive tools for energy plants. |
Top Swiss Security Companies for Critical Infrastructure (Europe & GCC)
This table lists leading Swiss companies specializing in critical infrastructure protection, offering cybersecurity, access control, and defense systems for both European and GCC regions.
| Company | Description | Website |
|---|---|---|
| Dormakaba Group | Leading provider of access control and physical security systems for airports, public institutions, and industrial infrastructure. | www.dormakaba.com |
| Kudelski Group (Kudelski Security) | Specialist in IoT and cybersecurity for critical digital infrastructure, including threat response and encryption services. | www.nagra.com |
| ImmuniWeb | Provides AI-driven cybersecurity tools, risk analysis, and dark web monitoring for critical sectors including energy, health, and telecom. | www.immuniweb.com |
| RUAG | Swiss government-owned defense company offering surveillance, satellite systems, and secure communications for critical defense and infrastructure. | www.ruag.com |
| Swissbit | Designs hardware security and storage devices for infrastructure requiring encrypted authentication and robust cyber protection. | www.swissbit.com |
These Swiss firms are ideal partners for resilient infrastructure projects in critical sectors such as energy, transportation, health, and defense.





Comments
Post a Comment